Google earth
My house 99/38 Pai-Kwang Subdistrict Muang District Suphanburi Province.
street view
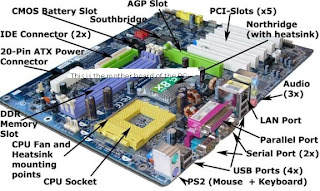 These facts may not solve all the hardware problems you may run into, however, they should solve a good number of them. The important thing to remember when trying to do any troubleshooting job, is that computers really are just logical devices and there is always a logical reason behind why things just not suppose to react the way they are. Finding what is that reason and then putting the right solution is not always easy, but if you approach the problem logically and work through it step-by-step, there is a very good chance you will be able to solve it by yourself.Examples are Expansion
These facts may not solve all the hardware problems you may run into, however, they should solve a good number of them. The important thing to remember when trying to do any troubleshooting job, is that computers really are just logical devices and there is always a logical reason behind why things just not suppose to react the way they are. Finding what is that reason and then putting the right solution is not always easy, but if you approach the problem logically and work through it step-by-step, there is a very good chance you will be able to solve it by yourself.Examples are Expansion The first academic work on the theory of computer viruses (although the term "computer virus" was not used at that time) was done in 1949 by John von Neumann who gave lectures at the University of Illinois about the "Theory and Organization of Complicated Automata". The work of von Neumann was later published as the "Theory of self-reproducing automata". In his essay von Neumann described how a computer program could be designed to reproduce itself.
The first academic work on the theory of computer viruses (although the term "computer virus" was not used at that time) was done in 1949 by John von Neumann who gave lectures at the University of Illinois about the "Theory and Organization of Complicated Automata". The work of von Neumann was later published as the "Theory of self-reproducing automata". In his essay von Neumann described how a computer program could be designed to reproduce itself..jpg) The first theory about software was proposed by Alan Turing in his 1935 essayComputable numbers with an application to the Entscheidungsproblem (Decision problem).[3] The term "software" was first used in print by John W. Tukey in 1958.[4]Colloquially, the term is often used to mean application software. In computer science andsoftware engineering, software is all information processed by computer system, programs and data.[4] The academic fields studying software are computer science and software engineering.
The first theory about software was proposed by Alan Turing in his 1935 essayComputable numbers with an application to the Entscheidungsproblem (Decision problem).[3] The term "software" was first used in print by John W. Tukey in 1958.[4]Colloquially, the term is often used to mean application software. In computer science andsoftware engineering, software is all information processed by computer system, programs and data.[4] The academic fields studying software are computer science and software engineering.